零、背景
笔者需要在米尔电子(MYIR)的MYD-YT113X(T113-S3)开发板上使用MQTT。首先就需要将MQTT通过交叉编译,移植到板子上。这一步已经完成,参见笔者(系列)文章:
从0到1玩转MYD-YT113X全志开发板 —— 移植MQTT(1)-CSDN博客
但如果要通过C语言代码实现MQTT功能,并在其中使用JSON功能,就需要在开发板上移植cJSON以及openssl,本文就来讲解openssl的详细移植过程。
一、基础工作
笔者鉴于之前移植SQLite3时的教训,不再通过传统一般性步骤:官网下载源码;配置交叉编译工具;编译构建;安装。而是先看开发板上是否已经有了openssl相关可执行文件和库。在开发板的/user/bin以及/usr/lib/下搜索“*ssl*”,结果如下:
root@myd-yt113-s3:~# find /usr/bin/ -name "*ssl*"
root@myd-yt113-s3:~#具体看一下/usr/bin/下的各文件:
root@myd-yt113-s3:~# ls /usr/bin/
'[' cx18-ctl isotprecv pon timeout
'[[' dbus-cleanup-sockets isotpsend pr tinycap
adbd dbus-daemon isotpserver printf tinymix
alsamixer dbus-launch isotpsniffer prlimit tinypcminfo
amixer dbus-monitor isotptun ptx tinyplay
amp_shell dbus-run-session ivtv-ctl python tinyplay_hub
aplay dbus-send jacd python3 top
ar dbus-test-tool jpegdecodedemo python3.7 tpadc_test
arecord dbus-update-activation-environment jspy python3.7m tplayerdemo
asc2log dbus-uuidgen jsr pyvenv tr
aserver dc killall rdiff traceroute
autplayer_test deallocvt last rds-ctl trecorderdemo
avahi-browse decode_tm6000 lcd_bright_test readlink truncate
avahi-browse-domains demoVencoder ldns-config realpath ts
avahi-publish diff less renice ts_calibrate
avahi-publish-address dircolors linux32 reset ts_conf
avahi-publish-service dirname linux64 resize ts_finddev
avahi-resolve dos2unix locale rev ts_harvest
avahi-resolve-address doveadm localedef rpbuf_demo tsort
avahi-resolve-host-name doveconf log2asc rpbuf_test ts_print
avahi-set-host-name dsync log2long rpmsg_demo ts_print_mt
awk du logger rpmsg_test ts_print_raw
b2sum dvb-fe-tool logname rs485_read ts_test
backplaydemo dvb-format-convert look rs485_write ts_test_mt
base32 dvbv5-daemon lscpu runcon ts_uinput
base64 dvbv5-scan lsipc scp ts_verify
basename dvbv5-zap lslocks script tty
bc dvr_test lsns scriptreplay tvd_test_mmap
bcmserver easy_install lsof seq uart_test
bunzip2 easy_install-3.7 lspci setarch uart_test_232
bzcat eeprom_test lsscsi setfattr udevadm
bzcmp eject lsusb setkeycodes uname26
bzdiff encodertest lv_g2d_test setsid unexpand
bzegrep env lzcat setusbconfig uniq
bzfgrep evtest lzma sexp-conv unix2dos
bzgrep expand lzopcat sftp unlink
bzip2 expr mcookie sha1sum unlzma
bzip2recover factor md5sum sha224sum unlzop
bzless fallocate media-ctl sha256sum unxz
bzmore fbinit memtester sha384sum unzip
canbusload fincore mesg sha3sum uptime
can-calc-bit-timing find microcom sha512sum usbcam_test
candump flock mkfifo shred users
canfdtest fmt mkpasswd shuf uudecode
cangen fold mosquitto_passwd slcan_attach uuencode
cangw free mosquitto_pub slcand uuidgen
canlogserver fuser mosquitto_sub slcanpty uuidparse
canplayer gcore MQTTVersion smtpd.py.7 v4l2-compliance
cansend gdb namei sort v4l2-ctl
cansniffer gdbserver nettle-hash split v4l2-sysfs-path
cec-compliance getopt nettle-lfib-stream sqlite3 vdecoderdemo
cec-ctl gpadc_test nettle-pbkdf2 ssh vlock
cec-follower gpio_test nl ssh-add w
chcon groups nohup ssh-agent watchdog
choom head nproc ssh-copy-id wc
chrt hexdump nslookup ssh-keygen wget
chvt hexedit numfmt ssh-keyscan whereis
cksum hostapd_cli od stat which
clear hostid openvt stdbuf who
cmp hwmac-R ota-burnboot0 stream_player_test whoami
col id ota-burnuboot strings xargs
colcrt install parserdemo sum xmetademo
collectdctl ipcmk passwd svc xmlwf
collectd-tg ipcrm paste svok xplayerdemo
colrm ipcs patch tac xxd
column iperf3 pathchk tail xz
comm iptables-xml pinky tee xzcat
coreutils ir-ctl pip telnet yes
crontab ir-keytable pip3 test
csi_test_usrptr isosize pip3.7 testj1939
csplit isotpdump pkcs1-conv tftp
cut isotpperf poff time
root@myd-yt113-s3:~#也确实没有相关的。
再在/usr/lib/下搜索“*ssl*”,结果如下:
root@myd-yt113-s3:~# find /usr/lib/ -name "*ssl*"
/usr/lib/libevent_openssl-2.1.so.6.0.2
/usr/lib/libssl.so.1.1
/usr/lib/libevent_openssl-2.1.so.6
/usr/lib/python3.7/asyncio/sslproto.pyc
/usr/lib/python3.7/site-packages/pip/_vendor/urllib3/util/ssl_.pyc
/usr/lib/python3.7/site-packages/pip/_vendor/urllib3/contrib/pyopenssl.pyc
/usr/lib/python3.7/site-packages/pip/_vendor/urllib3/packages/ssl_match_hostname
/usr/lib/python3.7/site-packages/setuptools/ssl_support.pyc
/usr/lib/python3.7/ssl.pyc
/usr/lib/libssl.so
/usr/lib/libevent_openssl.so
/usr/lib/dovecot/libssl_iostream_openssl.so
/usr/lib/libdcrypt_openssl.so
root@myd-yt113-s3:~#这样看的话,似乎系统中已经有了openssl相关的库。
二、详细步骤
为了进一步验证系统镜像中是否已自带(编译)了openssl,在MYD-YT113X(T113-S3)开发板SDK的buildroot中,通过menuconfig看一下是否已经将openssl勾选上了。
1. 查看Buildroot中openssl相关选项是否已被勾选
(1)进入Buildroot menuconfig
进入宿主机T113工作目录执行./build.sh buildroot_menuconfig命令。实际命令及结果如下:
habit@ubuntu:~/work/myir/T113$ ./build
build/ buildroot/ build.sh
habit@ubuntu:~/work/myir/T113$ ./build.sh buildroot_menuconfig打开menuconfig配置界面后。如下图所示:
(2)查找定位openssl相关选项位置
输入'/',在其中搜索“openssl”,结果如下:

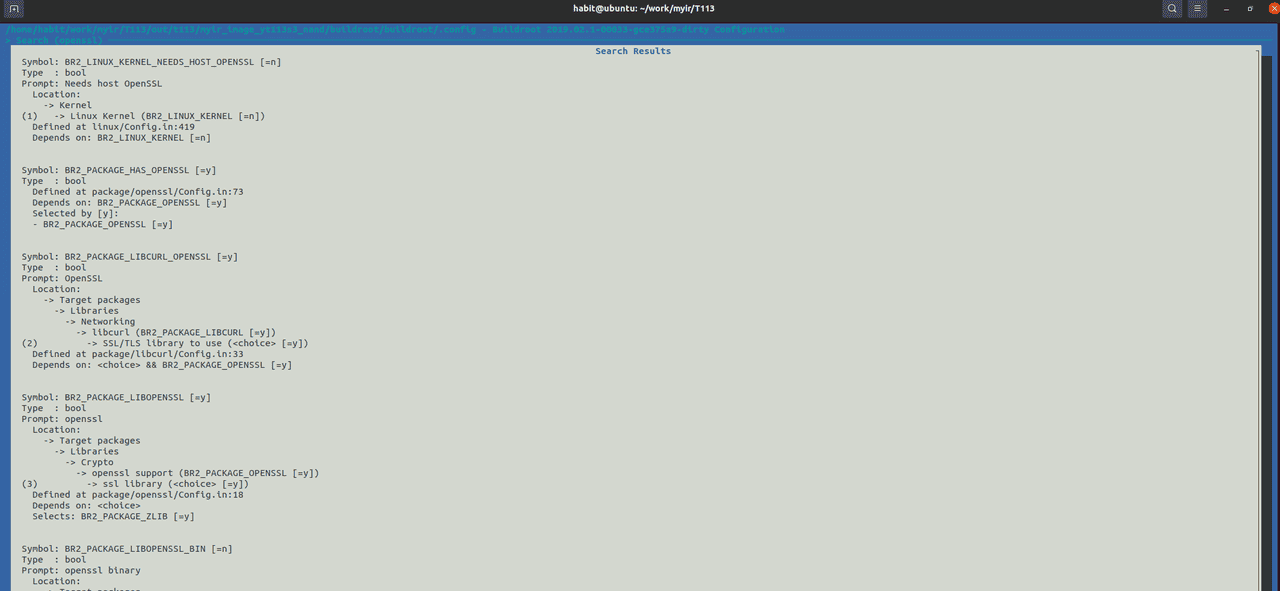
可以看到,openssl相关选项在“Target packages -> Libraries -> Crypto -> openssl support”下。
依次进入各界面,最终到其下:

可以看到,openssl相关的选项已经默认被选中了。

当然,默认并没有选中“openssl binary”、“openssl additional engines”,不过当前应该只用到openssl库,那两个选项不选也没太大影响。
这样,就验证了openssl库默认已经被编译进Buildroot了,与在开发板上的/usr/lib/下的发现一致。也就说明,在MYD-YT113X(T113-S3)开发板上,无需专门移植openssl库了。
相关文章




